In this post, we continue our Autopilot hybrid join troubleshooting series. Previously, we discussed the process flow starting with Device Enrollment , followed by the Offline domain join process, and explored a troubleshooting scenario for ODJ failure
Once the device completes the Offline Domain Join process and restarts, the Enrollment Status Page (ESP) begins, provided it is configured and assigned to the device or user.
Here, we will delve into the different stages of the ESP, focusing specifically on the first category: Device Preparation, then we will continue with Device setup in a different post. These stages are relevant to any Autopilot scenario.
The Account Setup phase, however, differs between Azure AD join and hybrid join scenarios. We will address this phase specifically for Autopilot hybrid scenarios in a separate post.
For a complete guide on how to create the ESP and understand each settings it is explained very well in Microsoft document Set up the Enrollment Status page
Table of Contents
ESP: Device Preparation Category
In Device preparation category there are 4 steps:
- Securing your hardware.
- Joining your organization’s network.
- Registering your mobile for device management.
- Preparing your device for mobile management.
For user-driven Entra join and hybrid join scenario without pre-provisioning, the first three steps will show completed immediately, why?
Securing your hardware: This step for TMP attestation that is done during Self-Deploying or pre-provisioning scenarios, so it is not applicable here and will show as completed.
Joining your organization’s network: This step to register the device in Azure AD, which is already done.
Registering your mobile for device management: This step to enroll the device in Intune, which already done also.
Then, Preparing your device for mobile management will start, let’s see what should be completed during this step
ESP: Device Preparation Category: Preparing your device for mobile management
During this step the ESP monitors the installation of policy provides, typically, the Intune Management Extension “SideCar” is the sole additional policy provider registered, although the ConfigMgr agent may also be present.
This step will be completed once the agent report that is installed successfully, or it is timeout and the installation of policy providers failed
Before digging deep in troubleshooting, if you need to get ESP settings from the logs you can do it using the following
- From registry dump file “MdmDiagReport_RegistryDump.reg”
[HKEY_LOCAL_MACHINE\software\microsoft\enrollments\xxxx\FirstSync]
“SyncFailureTimeout”=DWORD:000000f0
“BlockInStatusPage”=DWORD:00000003
“SkipDeviceStatusPage”=DWORD:00000000
“SkipUserStatusPage”=DWORD:00000000
- From event viewer “microsoft-windows-devicemanagement-enterprise-diagnostics-provider-admin.evtx”
events 357,358,355,356 & 354 will have some ESP settings value
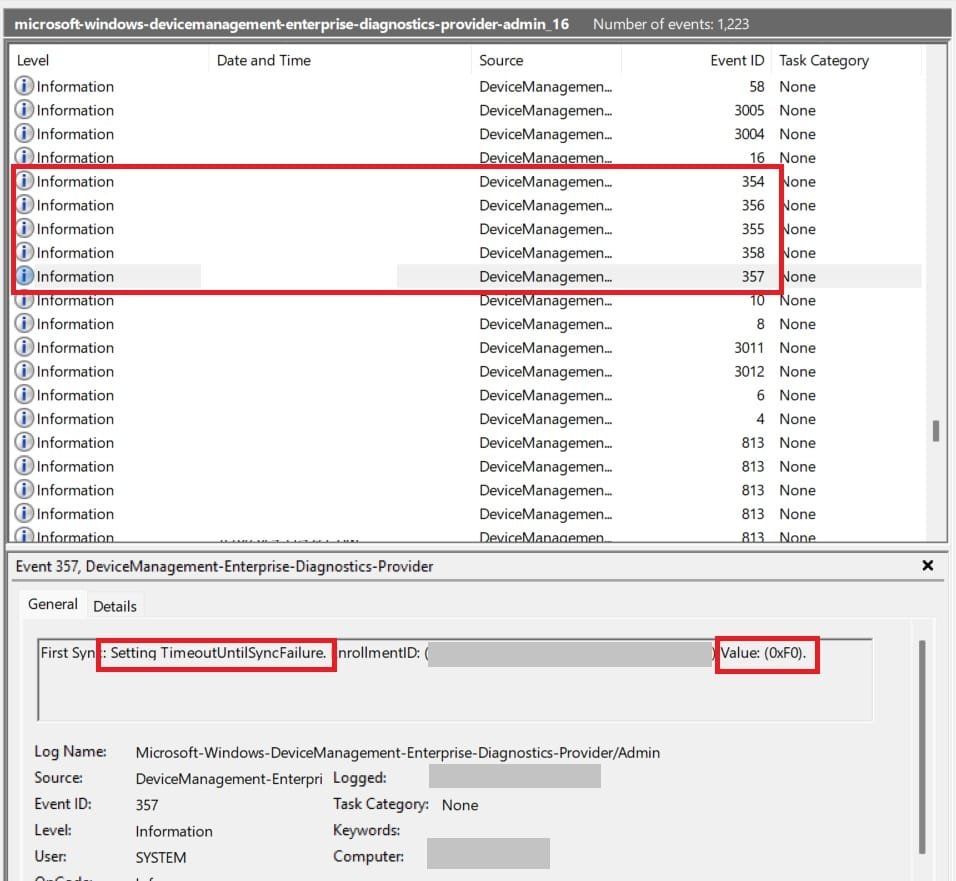
ESP: Preparing your device for mobile management troubleshooting
- From the Shell-core event viewer “microsoft-windows-shell-core-operational.evtx” we can confirm the status of each step
Starting DevicePreparationCategory
‘CommercialOOBE_ESPProgress_Category_Started’, Value: ‘{“message”:”BootstrapStatus: Starting category DevicePreparationCategory…”,”errorCode”:0}’.
Starting TPM Attestation
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_BootstrapStatusCategory_SubcategoryProcessing_Started’, Value: ‘{“message”:”BootstrapStatus: Starting subcategory DevicePreparation.TpmAttestationSubcategory…”,”errorCode”:0}’.
TPM attestation skipped and report succeeded
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_ESPDevicePreparation_TPMAttestation_NotRequiredForScenario’, Value: ‘{“message”:”Skipping TPM Attestation.”,”errorCode”:0}’.
‘CommercialOOBE_BootstrapStatusCategory_SubcategoryProcessing_Success’, Value: ‘{“message”:”BootstrapStatus: Subcategory ID = DevicePreparation.TpmAttestationSubcategory; state = succeeded.”,”errorCode”:0}’.
Starting AADJ
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_BootstrapStatusCategory_SubcategoryProcessing_Started’, Value: ‘{“message”:”BootstrapStatus: Starting subcategory DevicePreparation.AadjSubcategory…”,”errorCode”:0}’.
AADJ skipped and report succeeded
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_ESPDevicePreparation_AADJProvisioning_NotRequiredForScenario’, Value: ‘{“message”:”AADJ Provisioning skipped.”,”errorCode”:0}’.
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_BootstrapStatusCategory_SubcategoryProcessing_Success’, Value: ‘{“message”:”BootstrapStatus: Subcategory ID = DevicePreparation.AadjSubcategory; state = succeeded.”,”errorCode”:0}’.
Starting MDM Enrollment
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_BootstrapStatusCategory_SubcategoryProcessing_Started’, Value: ‘{“message”:”BootstrapStatus: Starting subcategory DevicePreparation.MdmEnrollmentSubcategory…”,”errorCode”:0}’.
MDM Enrollment skipped and report succeeded
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_ESPDevicePreparation_MDMEnrollment_NotRequiredForScenario’, Value: ‘{“message”:”Skipping MDM enrollment.”,”errorCode”:0}’.
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_BootstrapStatusCategory_SubcategoryProcessing_Success’, Value: ‘{“message”:”BootstrapStatus: Subcategory ID = DevicePreparation.MdmEnrollmentSubcategory; state = succeeded.”,”errorCode”:0}’.
Starting policy providers installation
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_BootstrapStatusCategory_SubcategoryProcessing_Started’, Value: ‘{“message”:”BootstrapStatus: Starting subcategory DevicePreparation.EspProviderInstallationSubcategory…”,”errorCode”:0}’.
Waiting for policy providers installation
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_ESPDevicePreparation_PolicyProvidersInstallation_Started’, Value: ‘{“message”:”BootstrapStatus: Starting the wait for policy providers installation.”,”errorCode”:0}’.
IME added
Shortcut for application Microsoft Intune Management Extension with ID Microsoft.Management.Clients.IntuneManagementExtension and flags 0x31 is added to app resolver cache.
Policy providers installed successfully
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_ESPDevicePreparation_PolicyProvidersInstallation_Succeeded’, Value: ‘{“message”:”BootstrapStatus: All policy providers have successfully installed a list of policies.”,”errorCode”:0}’.
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_BootstrapStatusCategory_SubcategoryProcessing_Success’, Value: ‘{“message”:”BootstrapStatus: Subcategory ID = DevicePreparation.EspProviderInstallationSubcategory; state = succeeded.”,”errorCode”:0}’.
Device Preparation category succeeded
CloudExperienceHost Web App Event 2. Name: ‘CommercialOOBE_ESPProgress_Category_Success’, Value: ‘{“message”:”BootstrapStatus: Category DevicePreparationCategory succeeded.”,”errorCode”:0}’.
- from registry dump file “MdmDiagReport_RegistryDump.reg”, this is a very useful log to get the status of the policy providers installation and get more details about it
open the file with notepad++ and search for “EnrollmentStatusTracking”, from the following key you can find the status of the policy providers installation “[HKEY_LOCAL_MACHINE\software\microsoft\windows\autopilot\EnrollmentStatusTracking\Device\DevicePreparation\PolicyProviders\Sidecar]”
- 1 (NotInstalled)
- 2 (NotRequired)
- 3 (Completed)
- 4 (Error)
[HKEY_LOCAL_MACHINE\software\microsoft\windows\autopilot\EnrollmentStatusTracking]
[HKEY_LOCAL_MACHINE\software\microsoft\windows\autopilot\EnrollmentStatusTracking\Device]
[HKEY_LOCAL_MACHINE\software\microsoft\windows\autopilot\EnrollmentStatusTracking\Device\DevicePreparation]
[HKEY_LOCAL_MACHINE\software\microsoft\windows\autopilot\EnrollmentStatusTracking\Device\DevicePreparation\PolicyProviders]
[HKEY_LOCAL_MACHINE\software\microsoft\windows\autopilot\EnrollmentStatusTracking\Device\DevicePreparation\PolicyProviders\Sidecar]
“InstallationState“=DWORD:00000003
“InstallDurationInSec”=DWORD:000000ce
If the state is in “Error” or “Not Installed”, The IME is a MSI app, so we can troubleshoot installation failure for MSI App
Then we can check the key “HKEY_LOCAL_MACHINE\software\microsoft\enterprisedesktopappmanagement\S-0-0-00-0000000000-0000000000-000000000-000\MSI{xxx}
Which gives useful information about the status of the IME installation and BITSJobID which can be tracked in event viewer “Bits-Client” for more details
“DownloadInstall”=”InProgress”
“ProductCode”=”{xxx}”
“ProductVersion”=”IME version“
“CreationTime”=
“ActionType”=
“Status”=DWORD:00000046
“JobStatusReport”=
“LastError”=DWORD:00000000
“BITSJobId”=”BITSJobID“
“DownloadLocation”=””
“DownloadUrlList”=MULTI_SZ:”https://naprodimedatapri.azureedge.net/IntuneWindowsAgent.msi”
“CurrentDownloadUrlIndex”=DWORD:00000001
“CurrentDownloadUrl”=”https://naprodimedatapri.azureedge.net/IntuneWindowsAgent.msi“
“FileHash”=”xxx”
“CommandLine”=””
“AssignmentType”=DWORD:00000001
“EnforcementStartTime”=QWORD:
“EnforcementTimeout”=DWORD:
“EnforcementRetryIndex”=DWORD:
“EnforcementRetryCount”=DWORD:
“EnforcementRetryInterval”=DWORD:
“LocURI”=”./Device/Vendor/MSFT/EnterpriseDesktopAppManagement/MSI/{xxx}/DownloadInstall”
“ServerAccountID”=”xxx”
for more details refer to the following techcommunity document
Also make sure that network requirements are met, as IME should be downloaded from CDN according to the location
- from Application event viewer log
The following events will show the status of the IME installation and version installed

Next posts we will continue with the device setup and Account setup categories




Leave a Reply