This article provides a step-by-step guide to using Microsoft Graph Explorer for modifying settings in iOS device restriction policies. Specifically, we will focus on adding apps to the “Show or Hide Apps” list in the App list of an iOS device restriction policy.
The admins can user Intune portal to modify the “Show or Hide Apps” setting to specify the iOS apps that user can/cannot view.
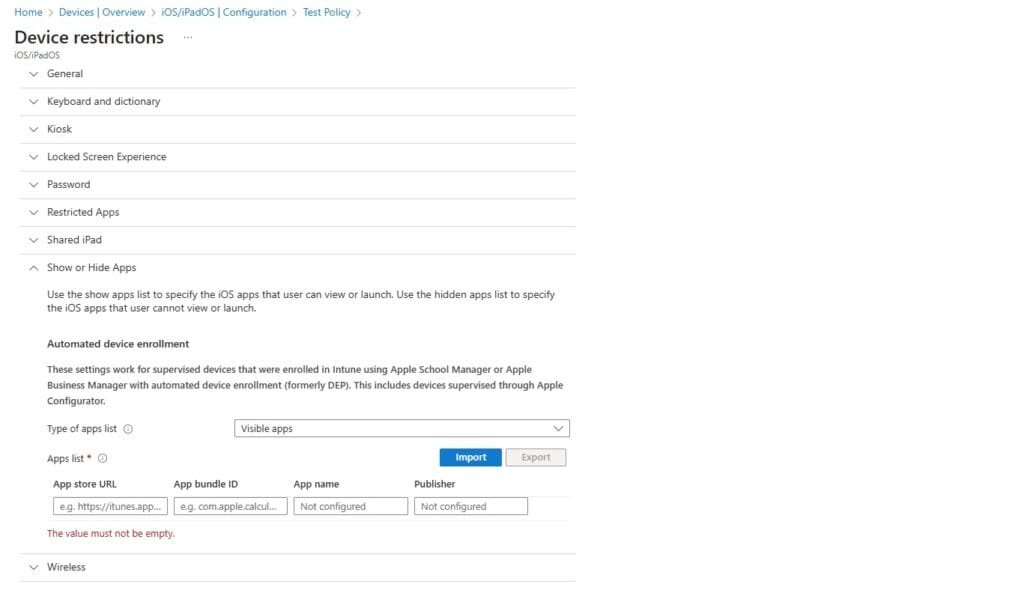
Table of Contents
Using Microsoft Graph – Analysis
in some scenarios the admins need to do the same from Graph, it could be for bulk updates or for scripting and automation
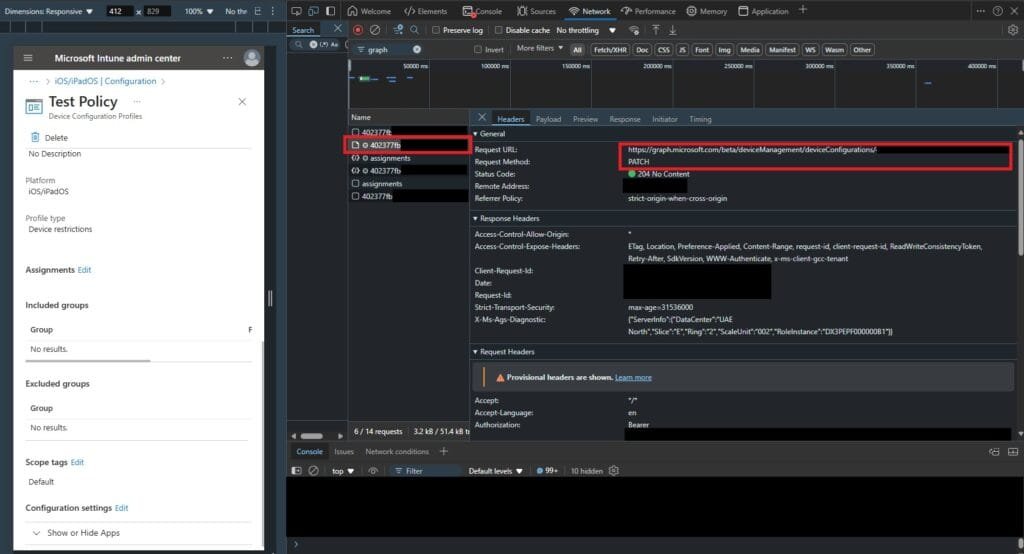
To see which query used we can do the action from the portal and enable Edge DevTools “F12”
from Headers we can get the query
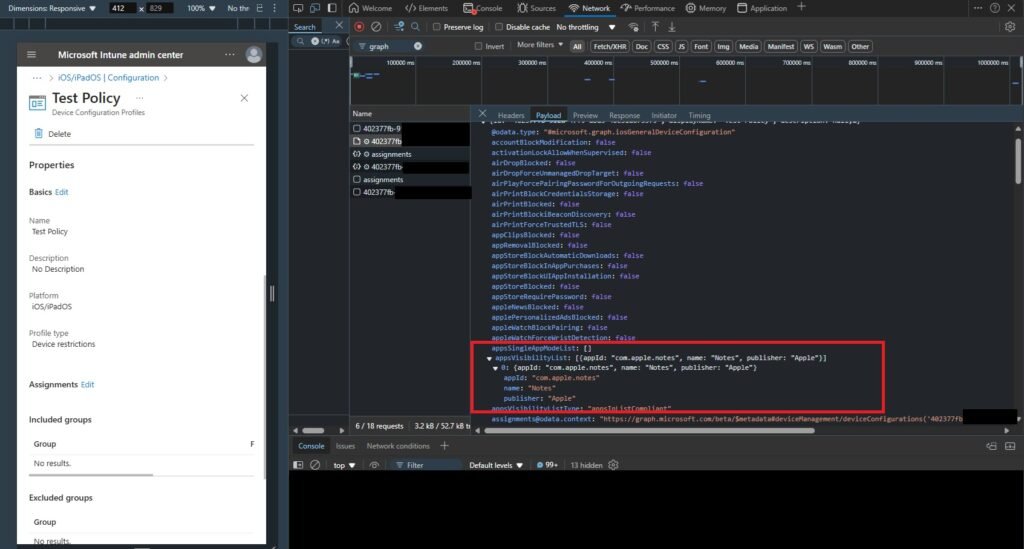
And from Payload to get the request body
Using Microsoft Graph – Testing
So the task involves performing a PATCH request to add apps to the App Visibility List within the iOS device restriction policy using the Graph API.
Steps to Follow
- Access Graph Explorer
- Open Microsoft Graph Explorer.
- Sign in with your administrator credentials to access the tenant resources.
- Prepare the Request
- Use the
PATCHHTTP method. - Construct the API endpoint as follows :
https://graph.microsoft.com/v1.0/deviceManagement/deviceConfigurations/{policy-id} - Replace
{policy-id}with the ID of the iOS device restriction policy you want to modify.
- Use the
- Define the Request Body
- The request body should contain the
appVisibilityListand specify theappVisibilityListTypeas either “Show” or “Hide”. Here is an example: { "appVisibilityList": [ { "name": "AppName", "publisher": "PublisherName", "appStoreUrl": "https://apps.apple.com/app-store-url", "appId": "com.example.app" } ], "appVisibilityListType": "Show" }
- The request body should contain the
- Send the Request
- Execute the
PATCHrequest in Graph Explorer and check for a successful response.
- Execute the
After running it, I go the following error message
Error Message
{ “error”: { “code”: “ModelValidationFailure”, “message”: “Exception has been thrown by the target of an invocation.” } }
Using Microsoft Graph – Solution
The error occurs due to improper request body structure.
- Use the same PATCH query
https://graph.microsoft.com/v1.0/deviceManagement/deviceConfigurations/{policy-id}- Replace
{policy-id}with the ID of the iOS device restriction policy you want to modify.
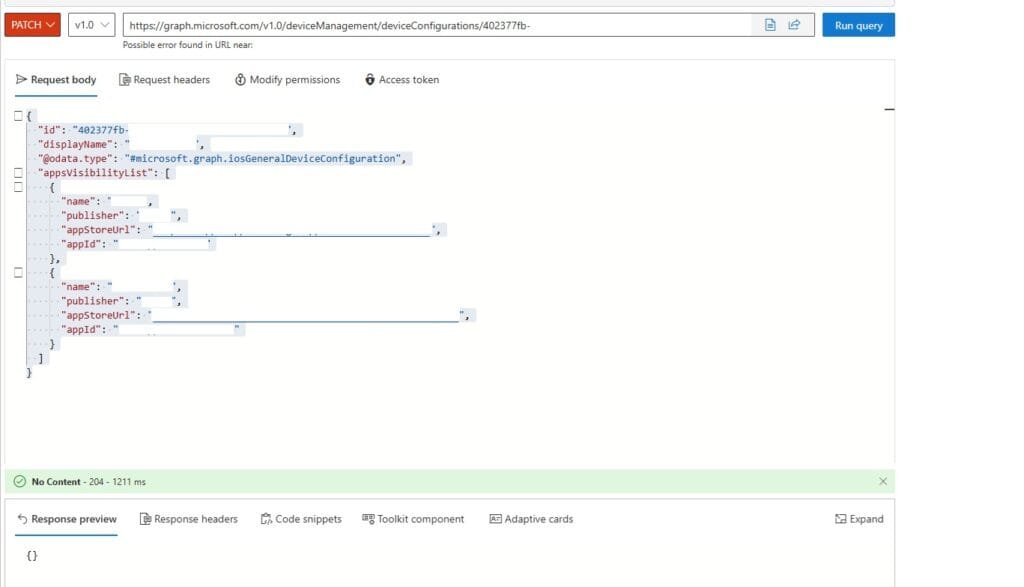
- Update the request body with accurate and complete app details. Here is an example of a working
PATCHrequest:
{
“id”: “PolicyID”,
“displayName”: “PolicyName”,
“@odata.type”: “#microsoft.graph.iosGeneralDeviceConfiguration”,
“appsVisibilityList”: [
{
“name”: “Name of the app”,
“publisher”: “App publisher”,
“appStoreUrl”: “Direct link to the app in the App Store”,
“appId”: “App bundle identifier”
},
{
“name”: “Name of the app”,
“publisher”: “App publisher”,
“appStoreUrl”: “Direct link to the app in the App Store”,
“appId”: “App bundle identifier”
}
]
}
Using Microsoft Graph – Verification
After sending the updated PATCH request, verify the changes:
- Use the
GETmethod to retrieve the updated policy and confirm theappsVisibilityListreflects the new entries. - Validate the changes on an iOS device managed under the updated policy.
Conclusion
Using Microsoft Graph Explorer to modify policies involves crafting precise API requests. and providing accurate details in the request body ensures successful updates.
Interested to read more articles from IntuneBytes, this is the link for all posts





Leave a Reply