Microsoft Intune provides a solution with its Application Protection Policies (APP) for iOS, designed to secure corporate data on mobile applications without compromising the user experience. This guide explores Microsoft Intune’s Application Protection Policies, focusing on how they work, why they’re essential, and how to implement them on iOS devices.
Table of Contents
What Are Microsoft Intune Application Protection Policies?
Microsoft Intune Application Protection Policies (APP) are a set of rules that secure corporate data at the application level on mobile devices. Unlike device-based policies, which manage an entire device, APP manages only the corporate data within applications.
This approach is often called Mobile Application Management (MAM), enabling companies to protect data on both company-owned and Bring Your Own Device (BYOD) scenarios.
For iOS, Intune APP allows IT administrators to apply specific policies to supported apps that contain company data. For example, they can enforce settings that prevent data leaks (such as copying data from a managed app to a personal app) or require authentication to access company resources within a mobile app.
Key Features of Intune Application Protection Policies for iOS
1. Data Separation and Security: APP keeps corporate data isolated from personal data on devices, preventing accidental data leaks between corporate and personal applications.
2. Application Selective Wipe: With selective wipe, administrators can remotely remove only the corporate data from an app without affecting personal data, ideal for BYOD and departing employees.
3. Data Transfer Restrictions: Policies can restrict or block data sharing between managed apps and unmanaged apps. For instance, users cannot copy and paste text from a corporate email app to a personal messaging app.
4. Access Requirements: Policies can enforce PIN codes, biometric authentication, or Corporate Credentials to access managed apps. These measures reduce unauthorized access to sensitive corporate data.
5. Conditional Access Integrating: APP with Conditional Access policies allows administrators to define access rules based on conditions like device compliance, location, or risk level. This integration ensures only authorized users in safe environments can access corporate resources.
6. Data Encryption: Corporate data within managed applications is encrypted, providing additional protection against unauthorized access if a device is lost or stolen.
Supported Apps for Intune Application Protection Policies on iOS
Intune APPs is integrated with Most of Microsoft Apps such as Microsoft Outlook, Teams, Microsoft Word, Excel, and PowerPoint.. etc.
Additionally, Third-Party Applications are also eligible to work with APP if they are integrated with Intune’s SDK or wrapped by Intune wrapping tool.
This is a list of All Microsoft Apps and 3rd Party Apps integrated with Intune-SDK and Support APP https://learn.microsoft.com/en-us/mem/intune/apps/apps-supported-intune-apps
Do I need to have any Broker-App installed?
Unlike Android, Microsoft Intune Application Protection policies are directly integrated with App and OS. Which means that Company Portal Application is not needed -as a broker App- for Application Protection Policies to work.
When enforcing Application Protection through Conditional Access Policies, users must have Microsoft Authenticator installed on their devices to sign in to any protected app. Microsoft Authenticator is required to collect device information and share it with Azure Conditional Access Policies for evaluating access compliance.
How to Create Intune Application Protection Policies for iOS
1. Log in to Microsoft Intune https://intune.microsoft.com
2. Create a New Policy – Go to Apps > App Protection Policies > Create Policy – Select iOS as the platform.
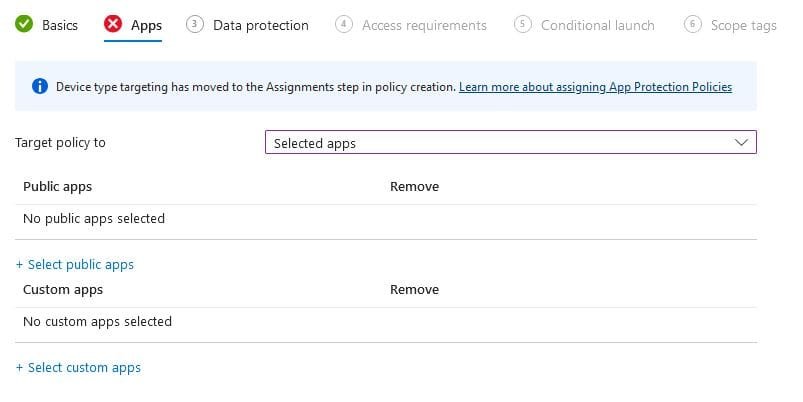
From App List you have the option to target APP to All Apps (Microsoft + 3rd Party Apps)
Or to All Microsoft Apps Or to Core Microsoft Apps only.
You have the option to select Public or Private Apps based on your needs.
3. Configure Policy Settings: Define Send Org Data (Where Corporate App will send data (share) to.
Save Copies of Corporate Data (e.g. OneDrive only or OneDrive and Local Drive.. etc.)
Best Practice for “Send Org Data” to be configured as “Policy Managed Apps with open-in/Share-Filtering”, this is designed especially for better user experience. When user decides to share Corporate Data, the share-to menu is going to display only Corporate Apps and will not show any other Personal Apps (like WhatsApp, TikTok.. etc.)
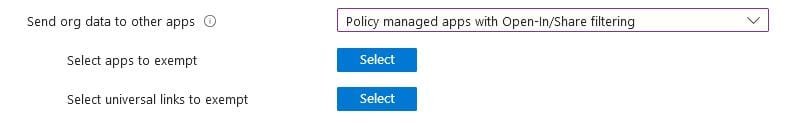
Receive Data from Other Apps (Where Corporate Apps will receive share from)
Encrypt Organization Data (to encrypt local data on all corporate Apps)
Set PIN Access for Corporate Apps (e.g. 8 PIN with Biometrics enabled or disabled)
Enable Access Requirements, such as enforcing PIN codes or biometric authentication.
Set Conditional Launch (e.g. define non-working hours action, define list of allowed Apple Models)
https://learn.microsoft.com/en-us/mem/intune/apps/app-protection-policies-access-actions
https://learn.microsoft.com/en-us/mem/intune/apps/app-protection-policy-settings-ios
4. Assign the Policy – Assign the policy to a specific user group within your organization.
Assignment should be including Managed App filter which specify what type of Device Management should include or exclude “assigned User group”
Managed Filter is NOT mandatory but should be used to enhance assignment.
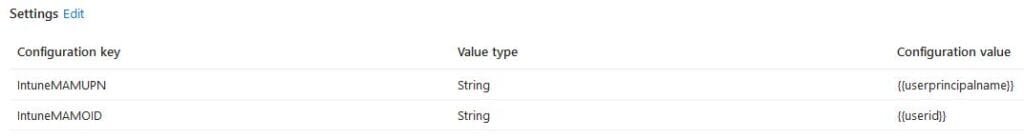
For the iOS devices when user is signing-in to any App, (and Unlike Android) Device is not sending Management Level to MDM Solution (Intune or other solutions). Hence, if the Administrator need device to check-in APP as Managed level. Then Administrator MUST send Application Configuration (Managed Device) Profile to every App to define Management Level.
For Example: Teams App MUST got App Config assigned to set IntuneMAMUPN as “{{userprincipalname}}” and IntuneMAMOID as “{{userid}}”
This is link for all Keys can be used with Intune APP + 3rd Party MDM https://learn.microsoft.com/en-us/mem/intune/apps/data-transfer-between-apps-manage-ios#example-1-admin-experience-in-intune-or-third-party-mdm-console
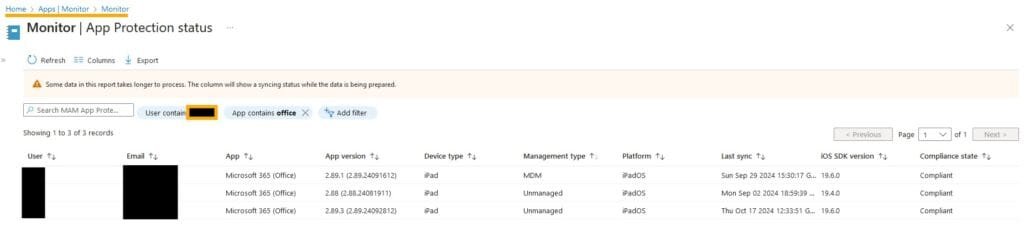
Reporting can be checked via: Intune Portal, Apps, Monitor, App Protection Status.
You can see in the below snapshot that device can check-in APP as Managed or Unmanaged based on Admin Choice (If IntuneMAMUPN is defined it’ll enforce MDM Check-in).
End-User Experience:
1- User open the App targeted with APP and enter credentials.
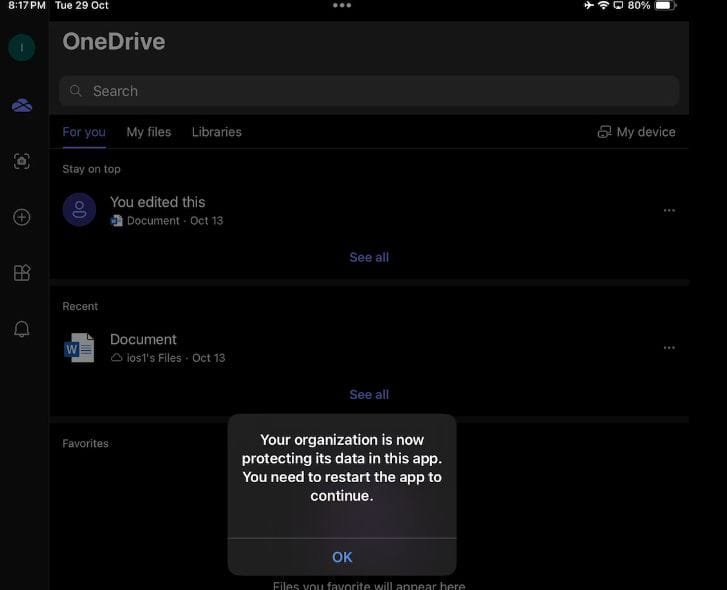
2- After completing Authentication, User will receive pop-up with Organization is now Protecting Organization Data.
And App will restart when clicking on OK.
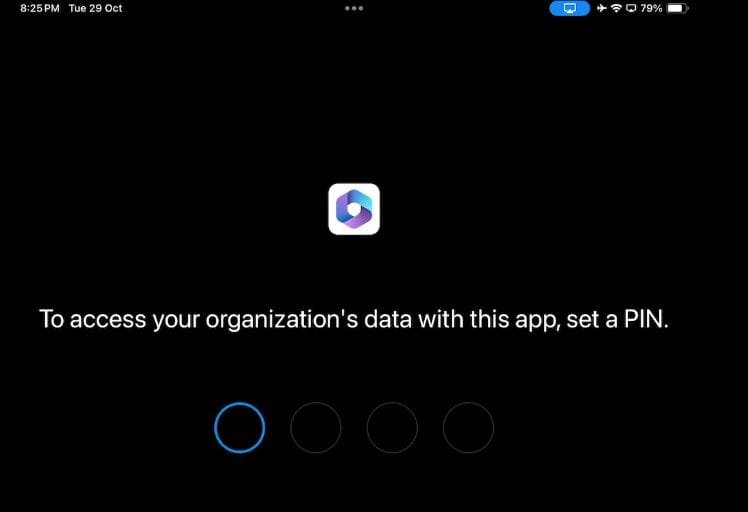
3- App will start again with enforcing Access Requirement.. for example Admin configured PIN to access the App.
Then user will be prompted to enter PIN (twice) before being allowed to access the App.
Best Practices for Implementing Intune APP on iOS Devices
1. Start with Pilot Testing Implement APP on a small group of users before a full-scale rollout. This pilot phase can help identify any issues and allow adjustments.
2. Communicate with Users Make sure employees understand the purpose and scope of APP policies, especially in BYOD scenarios. Transparency can ease privacy concerns and increase compliance.
3. Regularly Review and Update Policies Security threats and business needs change over time. Regularly reviewing APP settings ensures they stay effective against emerging threats.
4. Leverage Conditional Access Integrating Conditional Access policies with APP allows more granular control, enabling administrators to adjust app access based on specific conditions and requirements.
Conclusion
Microsoft Intune Application Protection Policies provide a robust and flexible approach to protecting corporate data on iOS devices, supporting both company-owned and BYOD environments. With features like data separation, selective wipe, access controls, and data loss prevention, Intune APPs allow organizations to secure data without intruding on user privacy or productivity. By following best practices in policy configuration and communication, companies can deploy these policies to maximize security, compliance, and user satisfaction.
Next Article to read Android Application Protection Explained





Leave a Reply